In this article, we will walk through the terraform module code to spin up a redundant RDS MySQL database service to run the NSOTapplication backend. Amazon Relational Database Service (Amazon RDS) makes it easy to set up, operate, and scale a relational database in the cloud. It provides cost-efficient and resizable capacity while automating time-consuming administration tasks such as hardware provisioning, database setup, patching and backups. It frees you to focus on your applications so you can give them the fast performance, high availability, security and compatibility they need.
The code we will be using is highly customizable with the ability to set your own instance sizes, data retention, DB snapshot, and backup schedules. We will be passing the following parameters to create a
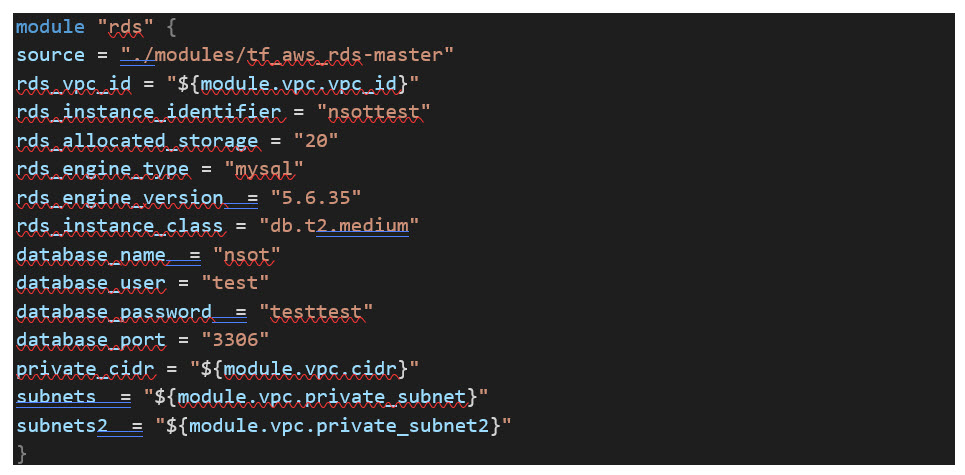
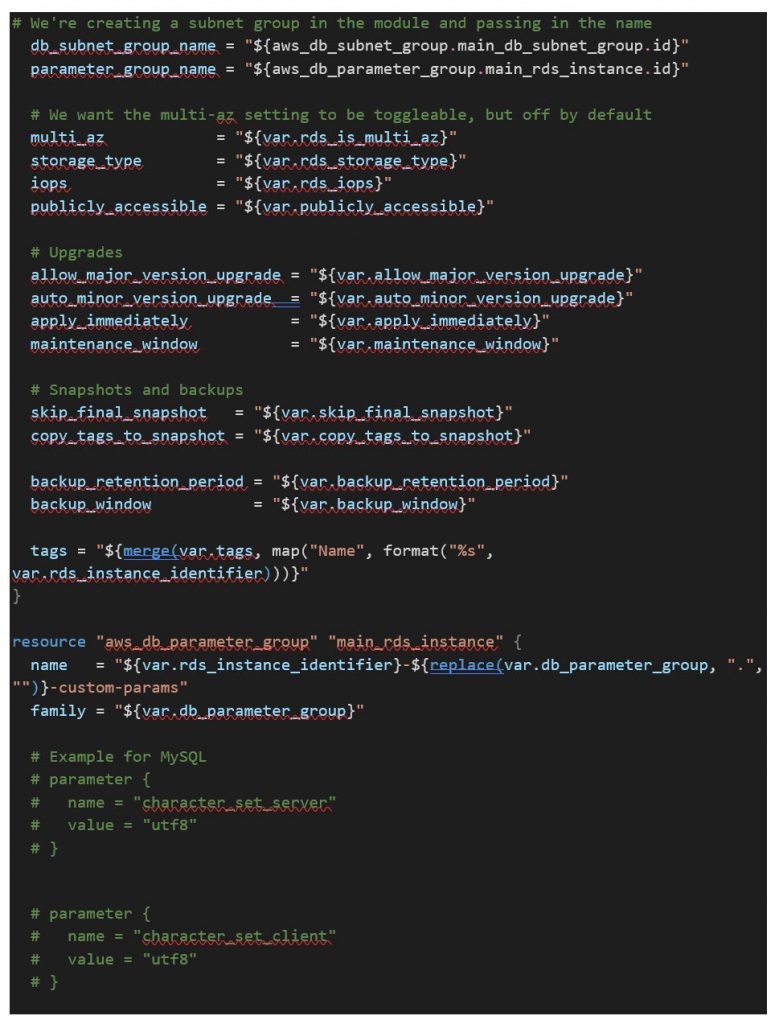
The first section of code creates the MySQL RDS instance(s), sets the DB name/identifier, listening port, username, password, etc. using the parameters passed
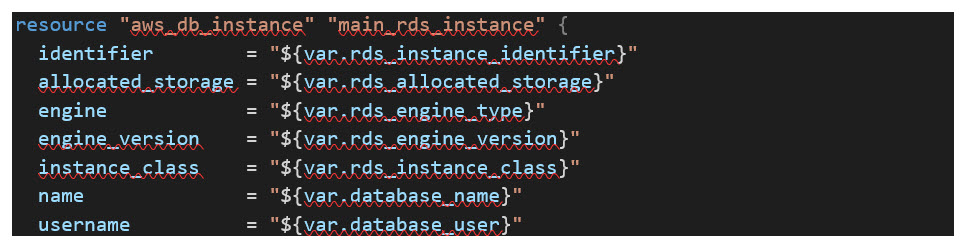
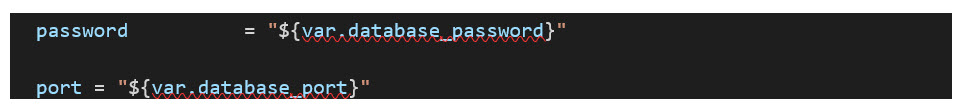
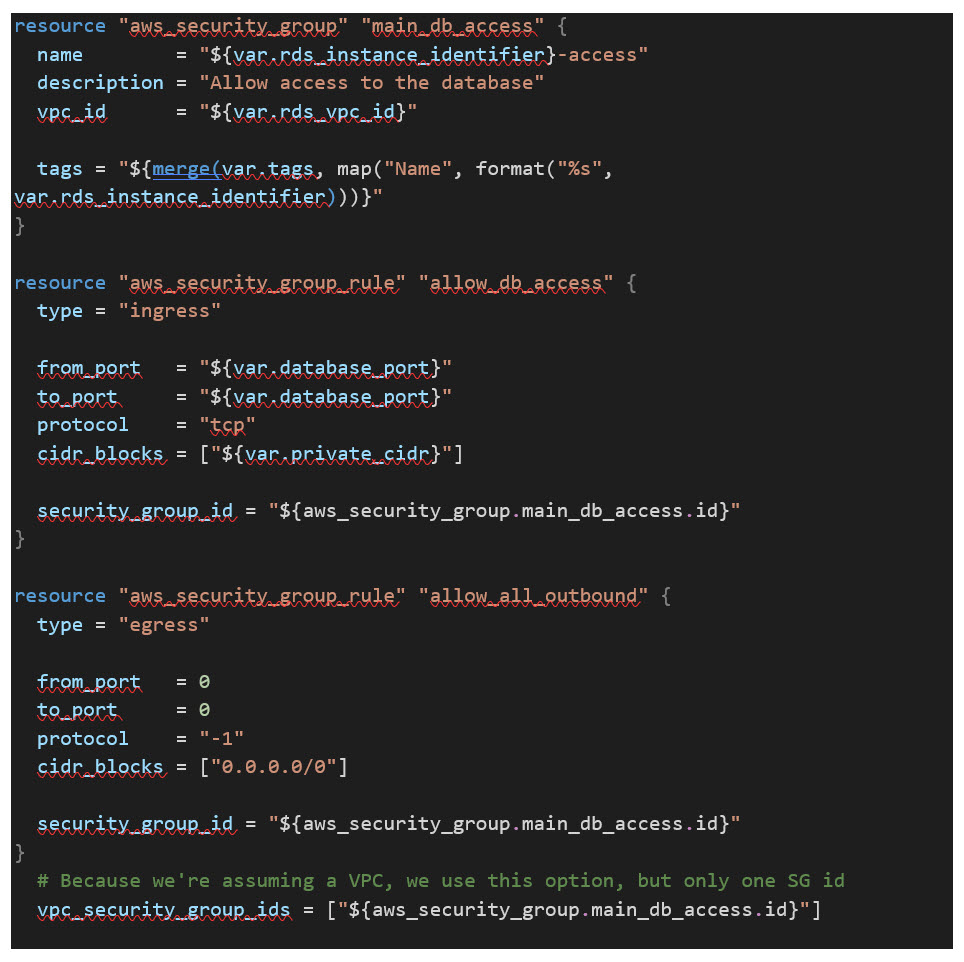
Next, the code below creates a security group to be applied to the MySQL RDS instance only allowing the necessary communication from the bastion
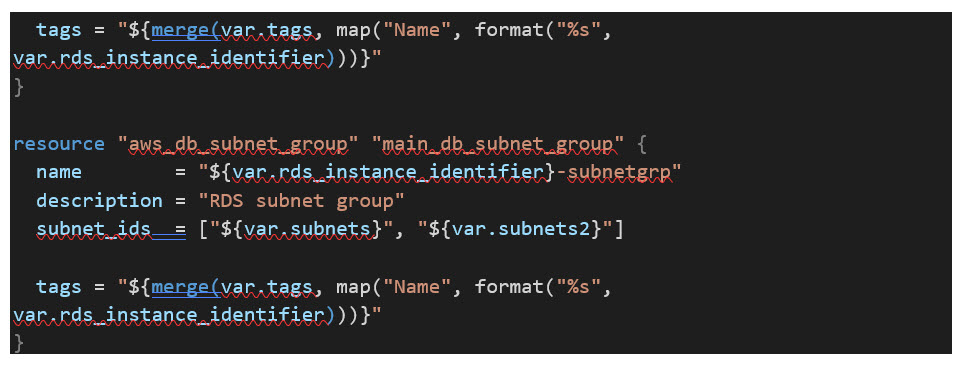
Next, we create the dedicated database subnet resources for the MySQL instances. Two subnets will be created as you cannot use a single subnet across two AZs.
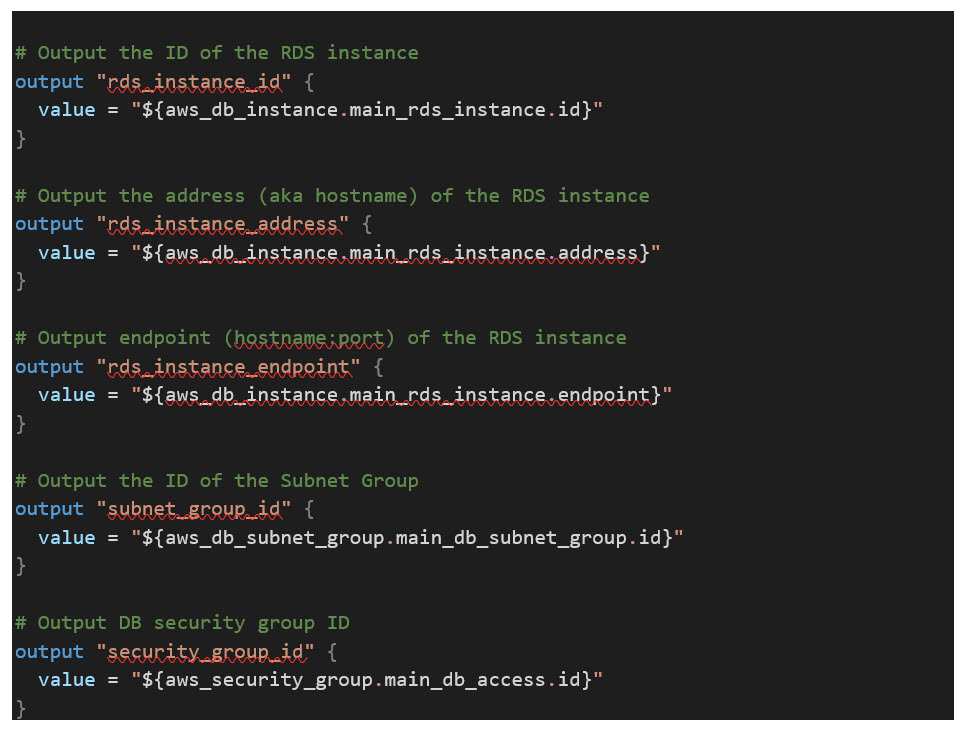
That’s it! You now have a working MySQL RDS module with automatic scheduled DB upgrades and backups for the